A recent class of FEMA’s Emergency Management Executive Academy published a paper titled Are We Prepared Yet? in the latest issue of the Domestic Preparedness Journal. It’s a solid read, and I encourage everyone to look it over.
First off, I wasn’t aware of the scope of work conducted in the Executive Academy. I think that having groups publish papers is an extremely important element. Given that the participants of the Executive Academy function, presently or in the near future, at the executive level in emergency management and/or homeland security, giving others the opportunity to learn from their insight on topics discussed in their sessions is quite valuable. I need to do some poking around to see if papers written by other groups can be found.
As most of my readers are familiar, the emphasis of my career has always been in the realm of preparedness. As such, it’s an important topic to me and I tend to gravitate to publications and ideas I can find on the topic. The authors of this paper bring up some excellent points, many of which I’ve covered in articles past. They indicate a variety of sources, including literature reviews and interviews, which I wish they would have cited more completely.
Some points of discussion…
THIRA
The authors discuss the THIRA and SPR – two related processes/products which I find to be extremely valuable. They indicate that many believe the THIRA to be complex and challenging. This I would fully agree with, however I posit that there are few things in the world that are both simple and comprehensive in nature. In particular regard to emergency management and homeland security, the inputs that inform and influence our decisions and actions are so varied, yet so relevant, that to ignore most of them would put us at a significant disadvantage. While I believe that anything can be improved upon, THIRA and SPR included, this is something we can’t afford to overly simplify.
What was most disappointing in this topic area was their finding that only a scant majority of people they surveyed felt that THIRA provided useful or actionable information. This leaves me scratching my head. A properly done THIRA provides a plethora of useful information – especially when coupled with the SPR (POETE) process. Regardless, the findings of the authors suggest that we need to take another look at THIRA and SPR to see what can be improved upon, both in process and result.
Moving forward within the discussion of THIRA and SPR, the authors include discussion of something they highlight as a best practice, that being New York State’s County Emergency Preparedness Assessment (CEPA). The intent behind the CEPA is sound – a simplified version of the THIRA which is faster and easier to do for local governments throughout the state. The CEPA includes foundational information, such as a factual overview of the jurisdiction, and a hazard analysis which ranks hazards based upon likelihood and consequence. It then analyses a set of capabilities based upon the POETE elements. While I love their inclusion of POETE (you all know I’m a huge fan), the capabilities they use are a mix of the current Core Capabilities (ref: National Preparedness Goal) and the old Target Capabilities, along with a few not consistent with either and a number of Core Capabilities left out. This is where the CEPA falls apart for me. It is this inconsistency with the National Preparedness Goal that turns me off. Any local governments looking to do work in accordance with the NPG and related elements, including grants, then need to cross walk this data, as does the state in their roll-up of this information to their THIRA and SPR.
The CEPA continues with an examination of response capacity, along the lines of their response-oriented capabilities. This is a valuable analysis and I expect it becomes quite a reality check for many jurisdictions. This is coupled with information not only on immediate response, but also sustained response over longer periods of time. Overall, while I think the CEPA is a great effort to make the THIRA and POETE analysis more palatable for local jurisdictions, it leaves me with some concerns in regard to the capabilities they use. It’s certainly a step in the right direction, though. Important to note, the CEPA was largely developed by one of the authors of the paper, who was a former colleague of mine working with the State of New York.
The Process of Preparedness
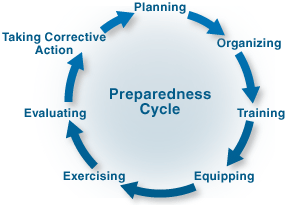
There are a few topic areas within their paper that I’m lumping together under this discussion topic. The authors make some excellent points about our collective work in preparedness that I think all readers will nod their heads about, because we know when intuitively, but sometimes they need to be reinforced – not only to us as practitioners, but also to other stakeholders, including the public. First off, preparedness is never complete. The cycle of preparedness – largely involving assessment, planning, organizing, equipping, training, and exercising – is just that – a cycle. It’s endless. While we do a great deal of work in each of these, our accomplishments are really only temporary.
The authors also mention that our information is not always precise. We base a lot of what we do in preparedness on information, such as a hazard analysis. While there are some inputs that are factual and supported by science, there are many that are based on speculation and anecdote. This is a reality of our work that we must always acknowledge. As is other of their points – there is no silver bullet. There is no universal solution to all our woes. We must constantly have our head in the game and consider actions that we may not have ever considered before.
ICS Improvement Officer
The authors briefly discuss a conceptual position within the ICS Command Staff they call the ICS Improvement Officer. The concept of this fascinating, if not a bit out of place in this paper given other topics of discussion. Essentially, as they describe this position, it is someone at the Command Staff level who is responsible for providing quality control to the incident management processes and implementations of the organization. While I’ve just recently read this paper and haven’t had a lot of time to digest the concept, I really can’t find any fault with the concept. While the planning process itself is supposed to provide some measure of a feedback loop, there isn’t anyone designated in the organization to shepherd that process beginning to end and ultimately provide the quality control measures necessary. In practice, I’ve seen this happen collaboratively, among members of the Command and General Staff of a well-staffed structure, as well as by the individual who has the best overall ICS insight and experience in an organization – often the Planning Section Chief. The authors elude to this position also feeding an AAR process, which contributes to overall preparedness. I like this idea and I hope it is explored more, either formally or informally.
Conclusion
There are a number of other topic areas of this paper which I haven’t covered here, but I encourage everyone to read on their own. As mentioned earlier, I’d like to see more of the research papers that come from FEMA’s Emergency Management Executive Academy available for public review. Agree or disagree with their perspectives, I think their discussions on various topics are absolutely worth looking at. It’s these discussions like these which will ultimately drive bigger discussions which will continue to advance public safety.
I’m always interested in the perspectives of my readers. Have you read the paper? What do you think of the discussion topics they presented?
© 2017 – Timothy M Riecker, CEDP
Emergency Preparedness Solutions, LLC