A few days ago I looked at four different links related to the 10 year anniversary of the US Department of Homeland Security (DHS). Every one of these links (here’s one of them) called for the abolishment of the department and decried everything they have done and stand for. Being the relative moderate that I am, I take a slightly different view on this – let’s make some changes, but in the end DHS will still stand – albeit a different agency.
On November 25, 2002 President George W. Bush signed into law the Homeland Security Act of 2002, which authorized the largest governmental reorganization in the US since the creation of the Department of Defense. The goal was to bring, in whole or in part, 22 US agencies which were chartered in some way with domestic terrorism protections under one agency umbrella. Interestingly enough, two agencies who took a lot of heat for perceived intelligence and coordination failures prior to the 9/11 attacks – the FBI and CIA – were not included in this reorganization… thankfully! It seems that over the last decade, nearly every entity brought into DHS has suffered in some way.
Looking back, there absolutely was a need for increased coordination amongst federal agencies when it came to intelligence. The US Intelligence Community is significant, with a multitude of agencies all playing a necessary role. In my humble opinion, there should have been a strengthening of the role and powers relative to intelligence coordination of the Director of National Intelligence. Perhaps even some agencies could have been merged, in whole or in part, to streamline missions.
Relative to the agencies brought into the fold of DHS, intelligence is a secondary or tertiary function to many of them (I speak of the function, not mental capacity). Similar to streamlining missions amongst intelligence agencies, certainly there could have been some mergers, again in whole or in part, amongst these 22 DHS-bound agencies to help streamline the response, training, and critical infrastructure missions that many of them touch upon. This would have had a much greater (positive) impact to the public safety and emergency management community than stuffing them all into one house and hoping they would get along. Despite intelligence not being a primary function of these agencies, DHS has jumped head first into the deep end of intelligence as a knee jerk reaction instead of going about it the right way. In this haste, we see some big mistakes with fusion centers, grabbing a lot of media attention. In government there tends to be a desire to over-legislate things. When we see a problem we create a bill and pass a law. That law creates a new agency or charges an existing agency to do something different. Often times, an existing agency is already doing what needs to be done or has the resources available to do it – which would be the easy fix. Instead we see something called mission creep, where agencies will wander into mission areas already occupied by someone else, and using some legal charter to justify the action. The creation of the US Department of Homeland security was the worst possible amalgamation of these circumstances, forcing changes in command structure and hierarchy of 22 different agencies – even taking away the cabinet-level position held by one of those agencies (FEMA) – a move that was realized as a significant mistake when Hurricane Katrina struck. The Washington Times even reports that President Bush was resistant to the concept, not seeing a need for such a large agency.
 DHS became a massive bureaucracy, not only through the merging of these 22 agencies, but through the creation of a substantial overhead organization. That overhead organization does little to provide shared services for those 22 agencies such as HR, payroll, purchasing, finance, etc. – which would be an ideal use. Instead, things grew so complex that for several years of the last decade, KPMG – one of the largest audit firms in the nation – was unable to complete an audit of the agency. Hundreds of billions of dollars have been budgeted to DHS over the last decade – dollar amounts far in excess of the value to the American public. Even their grants, which have benefitted many state, county, and local governments, have gone overboard and lack proper accountability. Some of the grant rules are so cumbersome that many jurisdictions haven’t been able to spend grant funds going back several years.
DHS became a massive bureaucracy, not only through the merging of these 22 agencies, but through the creation of a substantial overhead organization. That overhead organization does little to provide shared services for those 22 agencies such as HR, payroll, purchasing, finance, etc. – which would be an ideal use. Instead, things grew so complex that for several years of the last decade, KPMG – one of the largest audit firms in the nation – was unable to complete an audit of the agency. Hundreds of billions of dollars have been budgeted to DHS over the last decade – dollar amounts far in excess of the value to the American public. Even their grants, which have benefitted many state, county, and local governments, have gone overboard and lack proper accountability. Some of the grant rules are so cumbersome that many jurisdictions haven’t been able to spend grant funds going back several years.
But should we get rid of DHS? I say no. The Department of Homeland Security, originally created as the Office of Homeland Security (prior to the Homeland Security Act) was charged with developing a national strategy to secure our nation from terrorist attacks to include the coordination of detection, preparation, prevention, response, and recovery efforts. The creation of DHS should have been a modest and conservative reflection of this original charter, drawing in the necessary agencies and resources to accomplish this mission. It should not have swallowed agencies that have their own distinct missions, those that functionally don’t belong under another agency (i.e. emergency management as a function of homeland security) or those who best function with cabinet-level representation (i.e. FEMA). Yes, I do stand in obvious defense of FEMA, but 21 other agencies were also impacted significantly by this.
It’s not too late to make the necessary changes. As I’ve said in the past – let’s be smart and use some common sense.
 I finally had a chance to read through Homeland Security Today’s publication of The Leading Edge Today. The January edition was focused on cyber security. The Producer’s Corner article (i.e. letter from the editor), cites a study and report compiled by Verizon and other entities from around the globe, including the US Secret Service. This report, called the 2012 Verizon Data Breach Investigations Report, is staggering. They cite 855 confirmed cases of enterprise data loss and say that most entities that are hacked aren’t aware of it for weeks or months – and are usually notified by someone else of the incident (i.e. law enforcement or an enterprise internet security firm). The remainder of the publication offers some good information and insight on trends and prevention activities in the realm of cyber security.
I finally had a chance to read through Homeland Security Today’s publication of The Leading Edge Today. The January edition was focused on cyber security. The Producer’s Corner article (i.e. letter from the editor), cites a study and report compiled by Verizon and other entities from around the globe, including the US Secret Service. This report, called the 2012 Verizon Data Breach Investigations Report, is staggering. They cite 855 confirmed cases of enterprise data loss and say that most entities that are hacked aren’t aware of it for weeks or months – and are usually notified by someone else of the incident (i.e. law enforcement or an enterprise internet security firm). The remainder of the publication offers some good information and insight on trends and prevention activities in the realm of cyber security.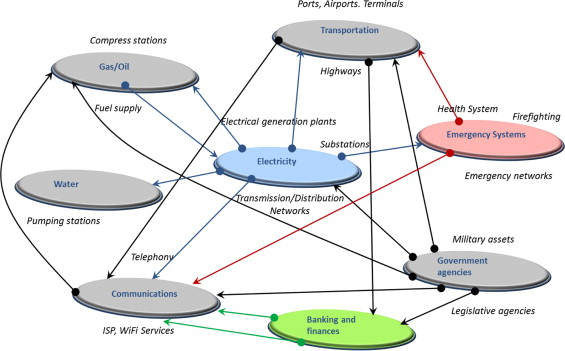

 Just read a
Just read a 



