Hello readers! It’s been a couple of months since I’ve last posted – along with the holidays, I’ve been fortunate to be busy with some great projects and a bit of travel. While I’m still busy, I’ve been itching to get back to posting.
Over the past few months, I’ve had an opportunity to look at some different aspects of incident action planning. Having worked as a Planning Section Chief for numerous state and federally declared disasters, I’ve created Incident Action Plans (IAPs), part and parcel, for a variety of incidents. Teaching hundreds of course offerings of ICS and EOC management, I’ve also had a lot of opportunity to help others understand and appreciate the value of an IAP.
What is an IAP?
The Incident Action Plan is really the culmination of the planning process. It documents our expected actions for the next operational period, which, through that planning process, should be ready to be supported through an identified organization and necessary resources. It begins, foundationally, with an understanding of the situation and objectives built to solve the problems that situation imposes upon us. IAPs identify some situational information, the incident objectives, and tactics – which specific resource assignments – to accomplish those objectives. To support the tactics, additional elements are added to the IAP, such as the organizational structure, a medical plan (for responders), a communications plan, and specific safety messages. Based upon the unique characteristics of each incident, additional material can be added.
The planning process, and thus IAPs, are a standard of practice within NIMS/ICS.
Issues with Teaching the Planning Process
For those coming up through the ranks, as it were, of ICS training, the forms integrated into ICS are often one of the most frustrating aspects. Responders want to do the hands-on stuff, not fill out forms. Most areas and systems, however, are able to find the responders who are interested in becoming involved in incident management aspects, and engage them in formal or ad-hoc incident management teams.
Often the only exposure that responders have to IAPs is from the ICS 300 course, where they are able to see some samples and are walked through the planning process and associated forms of the IAP. Having taught hundreds of these, I know it’s a challenge*. We inundate course participants with a pile of forms and expect them to leave the class to go out and do great things. While it might be a reasonable initial exposure, this needs to be followed up on, practices, and reinforced if we expect anyone to be successful, much less use the system.
*note: if you aren’t familiar with my position on the current state of ICS training, here are a few other blog posts to orient you. In short… ICS Training Sucks!
The planning process can be confusing – who does what? When? Based upon what information? The Planning P is the best visual out there and incident management handbooks (aka Field Operations Guides or FOGs) are references that every IMT member should have in the utility pocket of their 5.11s. While all based on the same system, I find the United States Coast Guard to have the best handbook out there. These are great job aids for something we don’t go to work and do every day, no matter how proficient you might think you are.
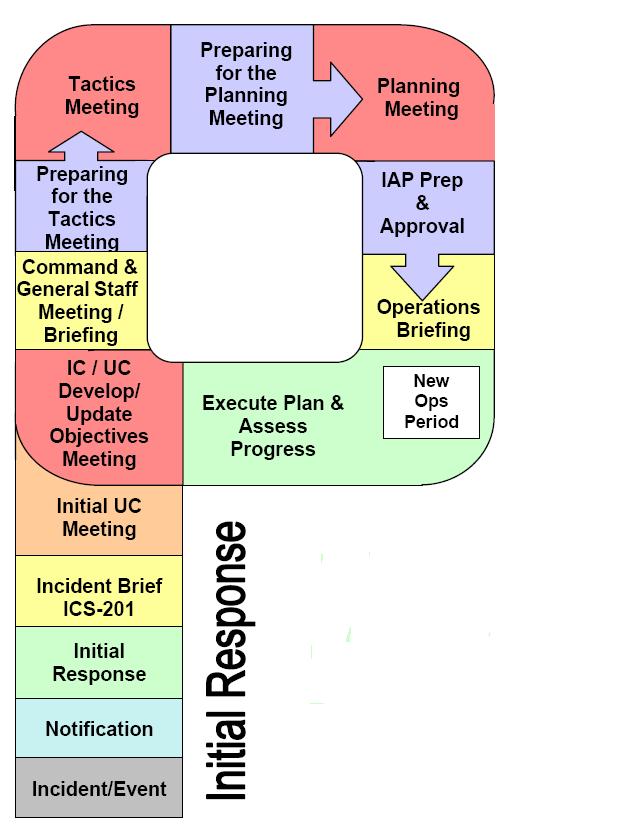
Uses of IAPs
IAPs can be applied to anything we can/should apply the planning process to. These include incidents, pre-planned events, and exercises. Planned events and exercises provide a great opportunity to practice the planning process and development of IAPs. It is certainly something that requires practice to be proficient. Every member of the Command and General staff, as well as a number of support positions, have an important role to play and responsibilities to contribute to the planning process. The forms themselves even require some practice to ensure that the right information is obtained. Large incidents can also require a great deal of tactical planning, which means greater time for that and for documenting the tactics and necessary support.
One aspect that is often forgotten in the heat of battle is that our response should, ideally, be based on our emergency operations plans (EOPs). These should be a regular reference to the Command and General staff, as they can, at the very least, provide some general guidance. Good EOPs, and their associated annexes, should provide some detailed guidance on certain aspects of response, which can prevent the IMT from having to re-invent a plan in the midst of chaos. The direction of EOPs, to the greatest extent possible, should be referenced in the planning process and reflected in the IAPs. EOPs should serve as the foundation for the planning process – with that in mind, EOPs can be implementation-ready. More thoughts on emergency plan development here.
As mentioned, exercises are a great opportunity for participants to practice the planning process and IAP development, along with other facets of ICS – especially those that we don’t get to apply so often. Also consider, however, the use of an IAP for exercise management. Our company, Emergency Preparedness Solutions, worked with the State of Vermont this past summer providing exercise control and evaluation services for their Vigilant Guard exercise. This week-long exercise spanned nearly 60 distinct venues across the state and involved thousands of participants. We coordinated over 100 control and evaluation staff throughout the exercise. While staffing decisions were made weeks in advance, we knew that with so many variables, needs and assignments were bound to change. For each operational period of the exercise, venues had staff assigned, a point of contact they should coordinate with, a need to communicate with the simcell and exercise management staff, a need to be aware of weather and safety matters, and processes to follow in regard to exercise management and reporting. We recognized the similarities to a tactical deployment and decided to develop incident action plans for exercise management. We called these eXercise Action Plans (XAPs). Within just a couple of operational periods, we were receiving great feedback on the documents from exercise staff. Use of XAPs were identified as a best practice in exercise management for that project.
Final Thoughts
Incident Action Plans are great tools that can help us put our emergency plans in action. They allow us to apply incident or event-specific ground-truths and the realities of incident needs and resources. While it’s understanding that some are frustrated with the forms used, the forms are job aids, tested through decades, to help us navigate complex incident management. When I walk into a command post or an EOC, the IAP is the first thing I look for. Because the format and forms are relatively standardized, I can flip through it, and in a couple of minutes have a good sense of the activity and who is responsible for what. Someone told me long ago that ICS is forms facilitated, not forms driven – and that’s very true. The forms (and thus the IAP) are products of the planning process, which is another decades-old practice in incident management.
What best practices have you seen in the application of the planning process and incident action plans?
Need assistance with planning, training, or exercises? Emergency Preparedness Solutions can help!
Until next time.
© 2017 – Timothy Riecker, CEDP