Inspired a bit by my previous post Measuring Return on Investment in Emergency Management and Homeland Security: Improving State Preparedness Reports, I’ve decided upon writing a series of posts picking apart our primary activities in emergency management and homeland security preparedness to identify ways to gauge our Return on Investment (ROI). To encapsulate our primary activities, I’m using the five POETE capability elements:
- Planning
- Organizing
- Equipping
- Training
- Exercises
Most preparedness activities within emergency management and homeland security fall within one or more of the POETE capability elements. The capability element of Planning is the foundational activity on which all preparedness is built and will be the topic of this post. Here’s what I’m covering:
- What is Return on Investment?
- What planning efforts are involved in preparedness?
- What organizational investments are involved in Planning?
- Does the planning effort comply with applicable standards?
- Can the plan be implemented?
- What will exercises tell you?
- Is there a need to maintain plans?
Return on Investment, or ROI, is a business term used to identify the profitability of certain investments or actions. While preparedness is certainly done to protect against losses, for public and private sector alike, we generally don’t see preparedness activities as generating revenue. However, when most entities INVEST time, money, and other resources into preparedness activities, they often want a reasonable assurance that their investment has paid off. How do we gauge ROI for planning efforts?
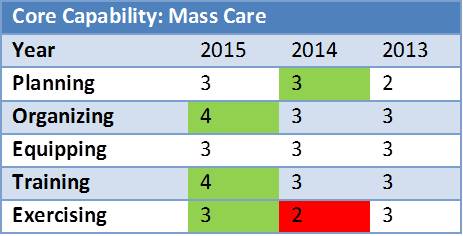
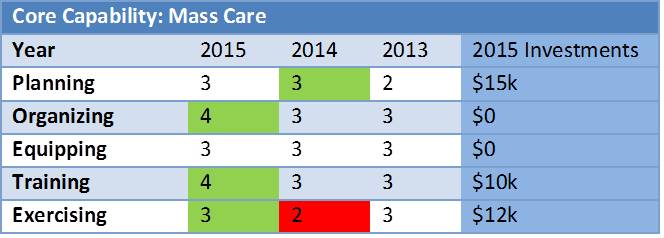
First off, what planning efforts might we see in public or private organizations? Obviously emergency and disaster plans are the big ones. These plans are designed to identify key processes, such as alert and notification, response organization and incident management, and others which are intended to save lives and protect property. These plans are likely to have annexes and appendices which address uniqueness of certain hazards, response circumstances, and support activities. Continuity plans – usually business continuity or government continuity – identify how the organization will survive as an entity in the face of disaster. Planning activities also involve the creation, review, and maintenance of policies and procedures. We also create plans for hazard mitigation, long term recovery, specific events, and other needs.
What investments are involved in planning activities? Organizations can and should allocate staff time and physical space and infrastructure to planning efforts. The dedication of staff (full or part time) and/or consultants is often required, especially when planning efforts are viewed as a continual process and a critical part of preparedness. The organization itself must make a commitment to the planning effort. This commitment isn’t just in concept, but also practical involvement of staff throughout the organization, access to information, and even an involvement of third parties.
Certainly a first step in assessing return on investment of planning is to evaluate compliance with applicable rules, regulations, and guidelines. These requirements can be hard (legally binding) or soft (general guidance) and can differ from industry to industry, nation to nation, and state to state. Here in the US, FEMA provides guidance on emergency planning through Comprehensive Preparedness Guide (CPG) 101. Some states may have requirements for emergency planning, such as New York State’s Executive Law Article 2-b. NFPA 1600: The Standard on Disaster/Emergency Management and Business Continuity Programs is often referenced by public and private entities alike, while the International Standards Organization (ISO), has many industry-specific requirements for emergency planning. If grant funding is being used for the planning effort, the grant may also have specific requirements. Regardless of what the requirements are, planning efforts, plans, and associated documents should be audited to ensure that requirements are met.
Compliance, however, isn’t necessarily indicative of a good planning effort. I’ve seen many plans which may meet requirements but the content itself was severely lacking. Far too often planners get caught up in the world of checking boxes and fail to consider implementation. If a plan cannot be implemented, it is useless to the organization. Many plans exist now that meet applicable requirements but are still yet vacant of any meaningful direction or guidance in the event of an emergency. These types of ‘plans’ are really better seen as policy documents. A plan should identify what will be done, when, how, and by who. If your ‘plan’ simply contains a statement on the requirement to use NIMS/ICS, but doesn’t provide detail on who will be in charge of what, when, and how; it is a policy document, not a plan. Plans and their associated documents (i.e. procedures, guidelines, and job aids) need to chase down the lifespan of each critical step, especially early in a response. They must identify who is responsible to make key decisions, who will be notified (how and by who), and who will take what actions. A logical review of planning documents by the planning committee or perhaps even a third party is another good means of assessing your return on investment.
Does the plan work? This is, perhaps, the ultimate factor in determining return on investment. Usually our best means for identifying if a plan works is to exercise it. Exercises provide a controlled and focused environment for testing plans or components of plans. They will also help us in identifying if the plan can truly be implemented. I’ve written a lot on exercises: articles can be found here. (I also anticipate writing about assessing ROI for exercises as part of this series). Generally, an incremental exercise program is usually recommended, beginning with discussion-based exercises – such as table tops and workshops – and progressing to operations-based (hands on) exercises. A well written and honestly evaluated exercise will go a long way toward identifying the return on investment of your planning efforts.
Are we there yet? Nope. Planning, like all other preparedness efforts, requires maintenance. If you create a plan then walk away, even if it’s a good plan, your plan’s value will diminish over time – and we’re talking months, not decades. Think about how often something changes in your organization. Staffing. Equipment. Technology. Procedures. Insurance policies. All of these things, and more, influence your plans in some way. Over time these changes not only occur, but also compound and move the present reality of your organization further from the assumptions of your planning efforts. This is why plans must be maintained and updated on a regular basis.
Is there some mathematical formula for identifying the return on investment of preparedness efforts? Given all the factors involved and their fluidity, I don’t think so. It’s not cut and dry like a traditional business investment. As you can see, though, there are a number of steps we can take to assess the utility of our investment. I’ve seen organizations pay a lot for bad plans, and others pay much less for great plans. Not only do organizations need to ensure that their planners know what they are doing, but the organization itself needs to have a commitment to success. Without it, the planning effort is doomed to fail.
As always, feedback is appreciated. What are your thoughts on assessing the return on investment of planning efforts? What do you think is a good measure?
Does your organization need a new plan or need to update a plan? Do you need help with the planning process or evaluating your organization’s preparedness? How about exercises? Emergency Preparedness Solutions can help! Email to consultants@epsllc.biz or visit www.epsllc.biz.
© 2015 – Timothy Riecker
Emergency Preparedness Solutions, LLC